A large amount of data is currently being stored in the cloud on a day-to-day basis, and much of this data is directly related to people's daily lives and various social activities. Protecting the privacy, confidentiality, and security of the information on the information infrastructure is also becoming increasingly important. On the other hand, such data need to be exchanged and analysed to achieve the effecient users' assistance. An privacy protecting information infrastructure that can distribute and process data to keep an appropriate level of privacy is essentially required.
Project Overview
Information Processing Infrastructure providing Privacy Control
Background
Concepts
In the proposed information infrastructure, the basic concept of protection is called Secure Network Containers. It is an information space that provides a certain level of privacy across networks for multiple software components, and data transfer to different privacy levels is realized by passing data between these secure network containers. Coceptually, handling of privacy data is processed with the consent of the user with preserving the appropriate level of privacy in each secure network container.
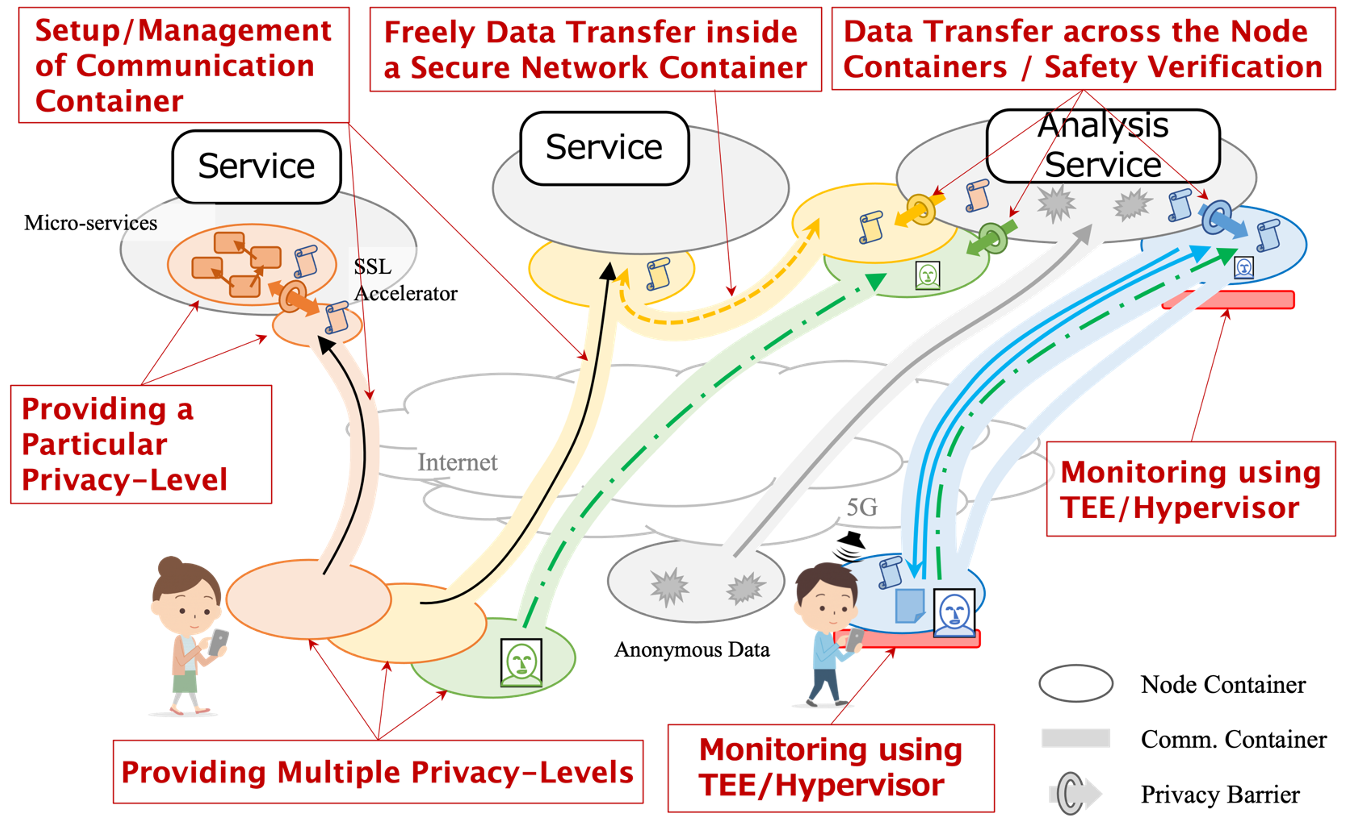
Research Topics
In order to realize the above concept, we are currently constructing an information processing infrastructure that integrates the two approaches of "data-level protection and system-level protection. The following specific research is being developed.
- Pseudonymized data exchange infrastructure to protect all data by pseudonymization
- Key information management infrastructure for appropriate re-identification of pseudonymized data according to a user's consent
- Monitoring mechanism for secure information exchange using TEE and virtualization
- Multi-layered/Distributed storage system to securely separate and store data according to privacy level
- Service execution and deployment mechanism on proposed privacy-centric information infrastructure
- Multimedia pseudonymization technology to protect data (mainly documents and audio)
- Security analysis mechanism based on a data flow type system for processing on the proposed information infrastructure